Are you vulnerable to the latest Java 0-day exploit?
Test to see if you're vulnerable.
The DeepEnd Research have been in contact with Michael Schierl
the Java expert who discovered a number of Java vulnerabilities,
including recent the Java Rhino CVE-2011-3544 / ZDI-11-305 and
CVE-2012-1723. We asked him to have a look at this last exploit .
Michael sent his detailed analysis, which we will publish in the nearest
future and a patch , which we offer on a per request basis today.
The Fix
There is no fix yet. The solution is disable Java plugin in all your browser to prevent malicious applets from running. The latest iteration of Java is version 1.7 revision 6. This is now the default version on Windows. Mac OS X still uses Java 1.6 (latest version: 1.6.33). Java 1.6.33 is NOT vulnerable to the latest 0-day exploit. However, I would not suggest that anybody downgrade from Java 1.7 to Java 1.6 as it is not yet known if version 1.6 is vulnerable to other flaws fixed in 1.7.
Firefox
Go to Tools - Add-ons - Plugins
Look for Java Deployment Toolkit and/or Java Platform SE. Disable them all.
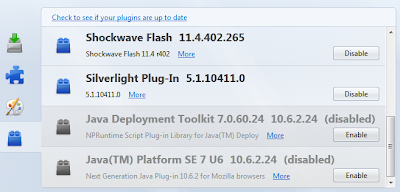 |
| Java disabled in Firefox |
Chrome
Go to Wrench - Settings and Show advanced settings... - Privacy and Content settings - Plug-ins - Disable individual plug-ins... - Java - disable. It is quite difficult to find!
 |
| Java enabled in Chrome |
Internet Explorer
Go to Tools - Manage Add-ons. Disable Java(tm) Plug-in SSV Helper and Java(tm) Plug-in 2 SSV Helper.
 |
| Java disabled in Internet Explorer 9 |
- http://research.zscaler.com/2012/08/are-you-vulnerable-to-latest-java-0-day.html
- http://www.deependresearch.org/2012/08/java-7-0-day-vulnerability-information.html

No comments:
Post a Comment